Anonymity Is No Longer Optional
by Jim Davidson
[email protected]
Special to L. Neil Smith’s The Libertarian Enterprise
Mechanic: Lemme tell you what you want. You wanna come and go like the wind.
Invincible, invulnerable, invisible.
Customer: And I want it Thursday at nine.
— Running Scared, film, 1986
You want to be free. You want to have your property safe from thieves. You want your communications safe from spies. You want your family safe from outrage. You want to be left alone and not be bothered by bullies or hoodlums or busybodies.
During the same period that the Internet was coming together there were two growing movements. One was open source software: better and thoroughly verified software that does exactly what the user wants. The other was public key cryptography, taking enormous strides toward communications privacy. Then, eleven years ago, came Bitcoin, combining these technologies.
These things brought the promise of financial autonomy, meaningful privacy, and real alternatives to the "trusted intermediary " model. We see from the proliferation of hundreds of billions of dollars worth of market capitalization in crypto-currencies, and the designs of many new currencies, that a great deal of work has been done. We can also see that the promise has not been met.
Surveillance technologies are very powerful. Chain analysis technologies combine "big data" with traffic analysis and careful examination of information included in transactions. Combined, these blow right through your privacy.
Privacy coins have developed to address parts of this problem, especially by mixing small transactions. But as long as your connection to the Internet reveals your location, you have no privacy.
Google Sits Athwart Your Web Browsing
You may not use Google search, and you may have a private email address that isn’t served by Google Suite. These are good choices on your part. But did you know that millions of web sites are built with Google tools? Even web portals dedicated to individual freedom have Google scripts embedded in their pages. Here’s an example.
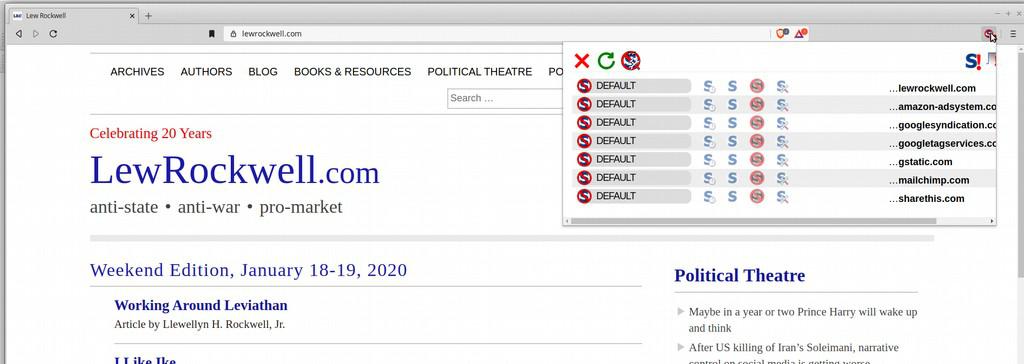
The upper right part of this screen capture above shows dialogue from NoScript. You can see that several Google-related sites and an Amazon site are involved. Loading the page with all of the scripts means that your web browsing activity is connected directly to Google. And we know (from WikiLeaks, Edward Snowden and others) that Google and other tech companies sell their data to corporations and governments world-wide.
The people who buy the data sets from Microsoft, Google, Apple, Amazon, Facebook, Twitter, and others know everything about you: Which sibling you communicate with most often, what you really think of your boss and more. Everything you say, everything you see, everything you buy, everything you do online can be monitored if you browse directly through a normal connection. And the companies that buy your data wouldn ’t part with their money unless they meant to use it in ways you wouldn’t.
You Can Be Anonymous
Since privacy, even with encrypted communications, is compromised when your communications are associated with your identity, what you need is anonymity. You really can’t be free without it.
How do you get it? With a multi-hop, multiple-jurisdiction virtual privacy network… with an anonymous VPN .
Multi-hop means two or more hops, so there is no direct tunneling. (A direct tunnel is a kind of VPN, but not a very effective one.) Two or more hops allow for traffic mixing and actual anonymity. Having the hops go through more than one jurisdiction makes tracing communications much more operationally complex.
A company which has provided effective multi-hop, multi-jurisdiction VPN services for many years is Cryptohippie.com. Their system is jurisdictionally aware and they have service options for both individuals and businesses.
Yes, there is "the onion router," or TOR, but it simply isn’t usable for general surfing. You can try it yourself and see.
If you want to be free you need anonymity; encryption alone is not enough. You can have private Internet communications only with anonymous access.
Jim Davidson sent his first email in 1978, started posting on USEnet in 1982, and has studied, used, and taught encryption since 1992. He has traveled in Europe, Asia, Africa, and North America, and is one of the few voluntaryists who has lived in Somalia. You can connect with Jim at flote.app/planetaryjim and elsewhere online such as KanehCN3.com
Was that worth reading?
Then why not:
![]()
|
Support this online magazine with
|
AFFILIATE/ADVERTISEMENT
This site may receive compensation if a product is purchased
through one of our partner or affiliate referral links. You
already know that, of course, but this is part of the FTC Disclosure
Policy
found here. (Warning: this is a 2,359,896-byte 53-page PDF file!)
L. Neil Smith‘s The Libertarian Enterprise does not collect, use, or
process any personal data. Our affiliate partners, have their own
policies which you can find out from their websites.
